Requirements permalink
- Windows 11
- Burp suite
- Python3
- Pip
Installing WSA (Windows subsystem for android) permalink
First search for windows features and enable hypervisor and virtual machine platform.
Then lets use MagiskOnWSA to install WSA and play store. See the video on how to install. Select pico for minimal google play apps and download the zip after the build finishes.
Magisk and Play store should pop up now, just sign in and close both.
Installing Frida Server And Objection permalink
Download frida-server latest x64 version and run the following commands. Objection uses frida as a backend so we need to run it first to use objection.
Then lets install objection. This will install objection, frida-ps, frida etc.
PS C:\Users\gamep> pip3 install objectionExport Burp Suite Certificate permalink
Now lets gather all the files like the certificate and frida-server to upload to the android device.
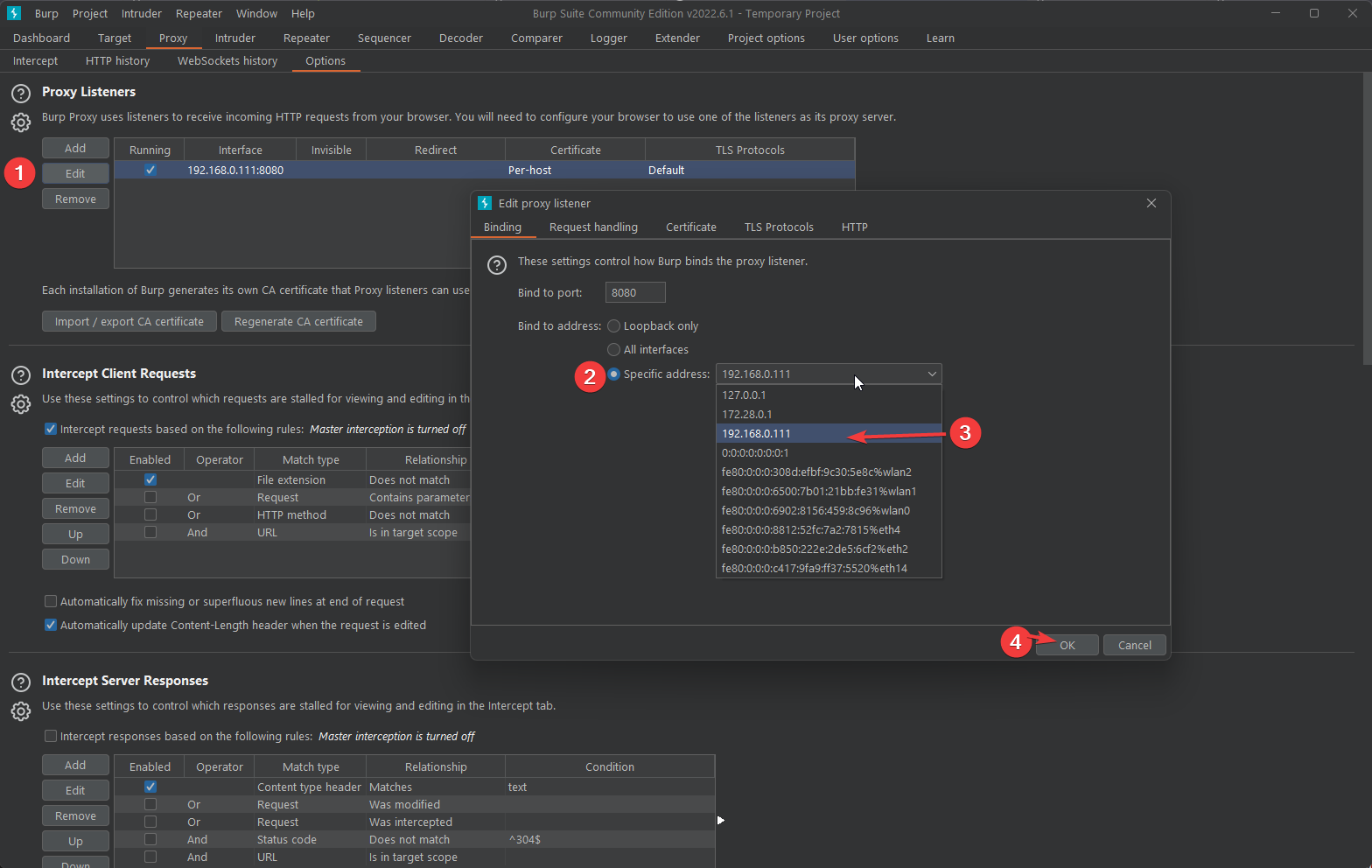
Lets bind the the correct address:
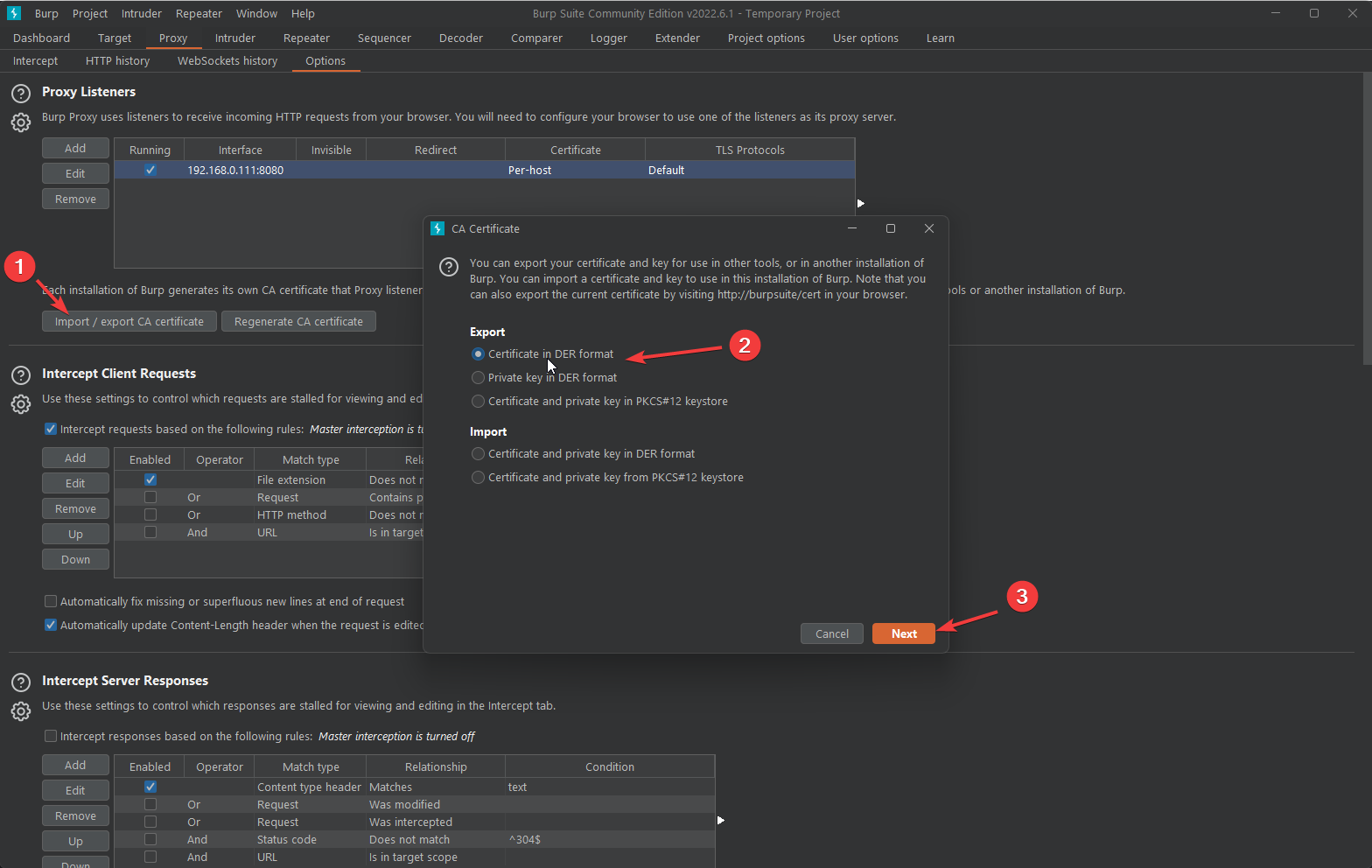
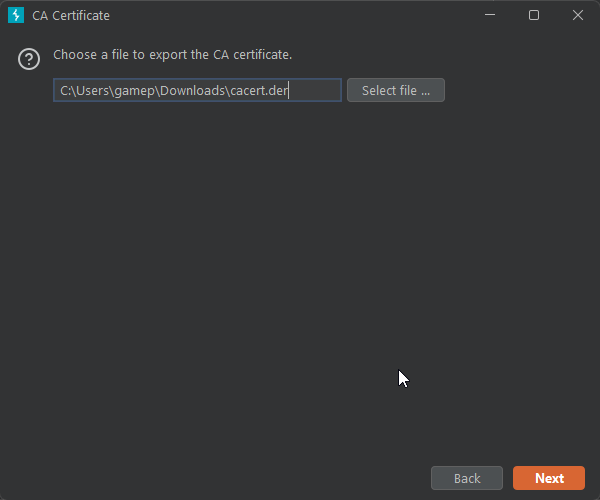
Now lets export the certificate:
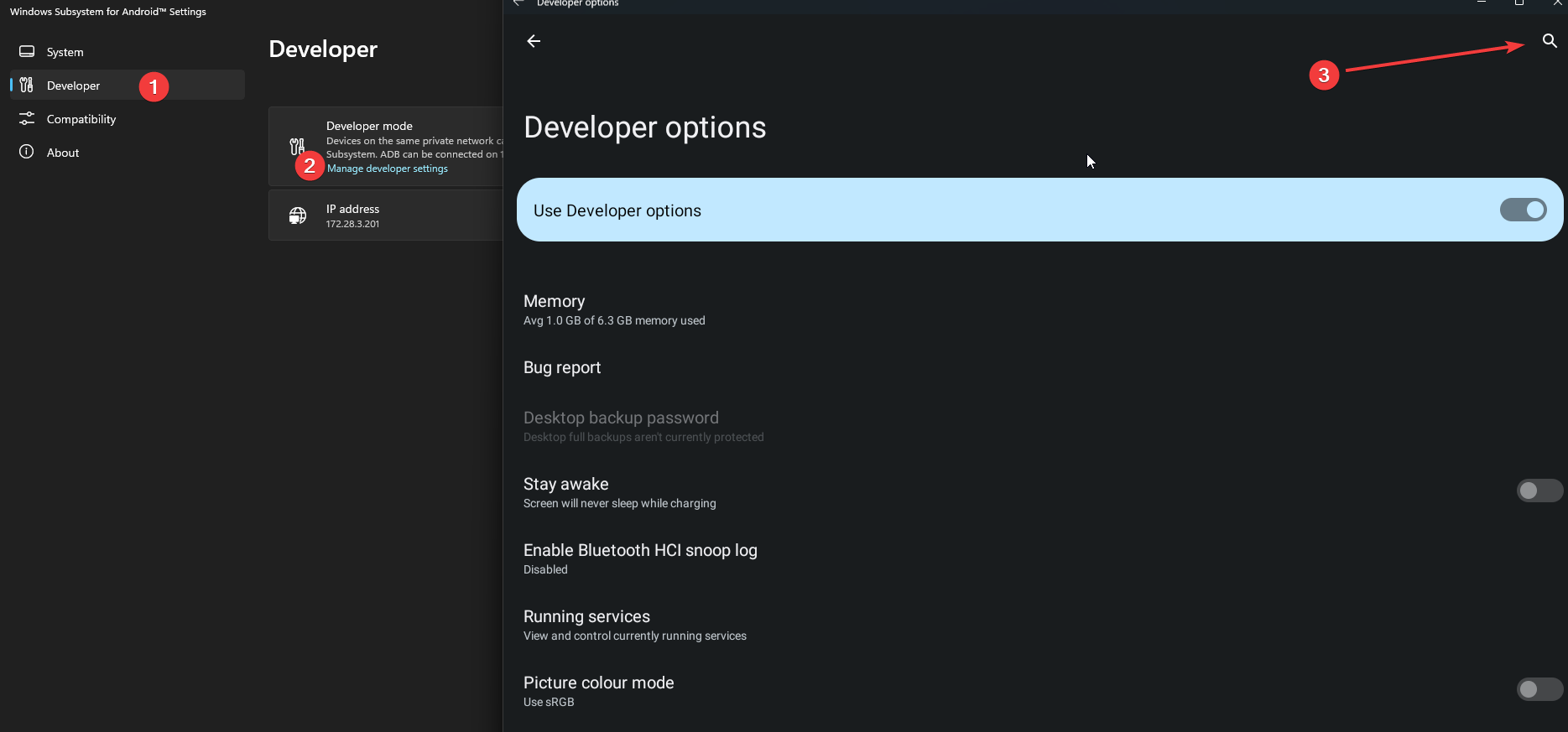
Enabling Developer Mode permalink
Now we need to enable developer mode so that we can connect to adb. Search for Android and goto developer tab and enable developer mode.
Setting up Frida Server And Objection permalink
PS C:\Users\gamep> adb connect 127.0.0.1:58526
adb:connected
PS C:\Users\gamep> adb push .\Downloads\frida-server-15.1.27-android-arm64 /data/local/tmp/frida-server
.\Downloads\frida-server-15.1.27-android-arm64: 1 file pushed, 0 skipped. 51.8 MB/s (47172184 bytes in 0.869s)
PS C:\Users\gamep> adb push .\Downloads\cacert.der /sdcard/Downloads
PS C:\Users\gamep> adb shell
redfin:/ $ cd /data/local/tmp
redfin:/data/local/tmp $ su
redfin:/data/local/tmp $ chmod 777 ./frida-server
redfin:/data/local/tmp # ./frida-server &
[1] 5023
redfin:/data/local/tmp # exitNow that the frida server is running lets setup the wifi proxy settings.
Wifi Proxy permalink
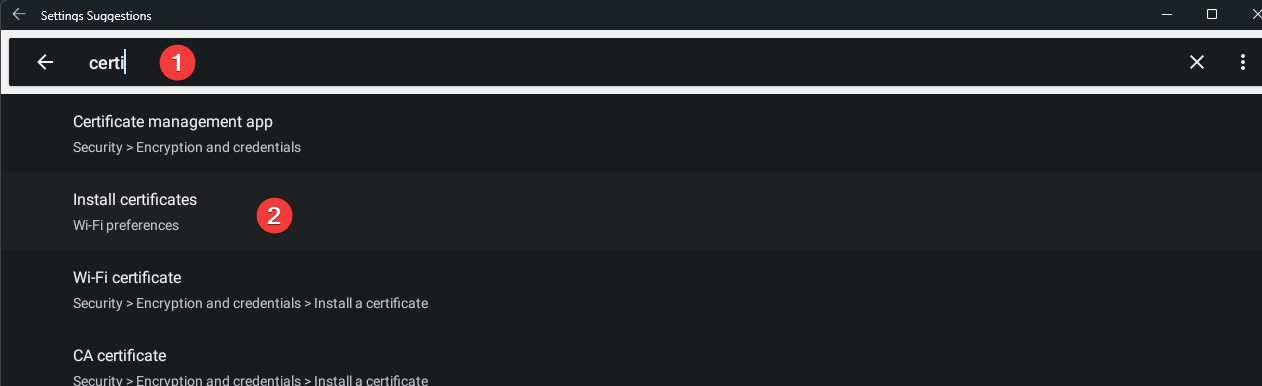
Search ceritifcate.
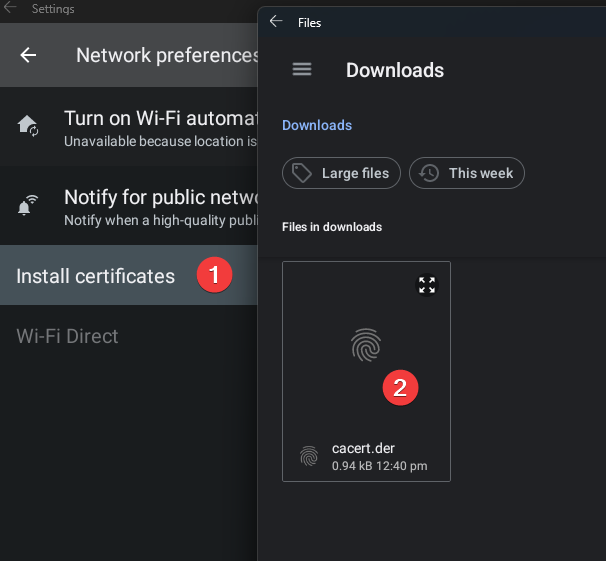
Great now the certificate is installed. Now search for wifi click edit and put your proxy ip and port is 8080 default (you have to use keyboard because there is some bug with mouse).
SSL Pinning Bypass permalink
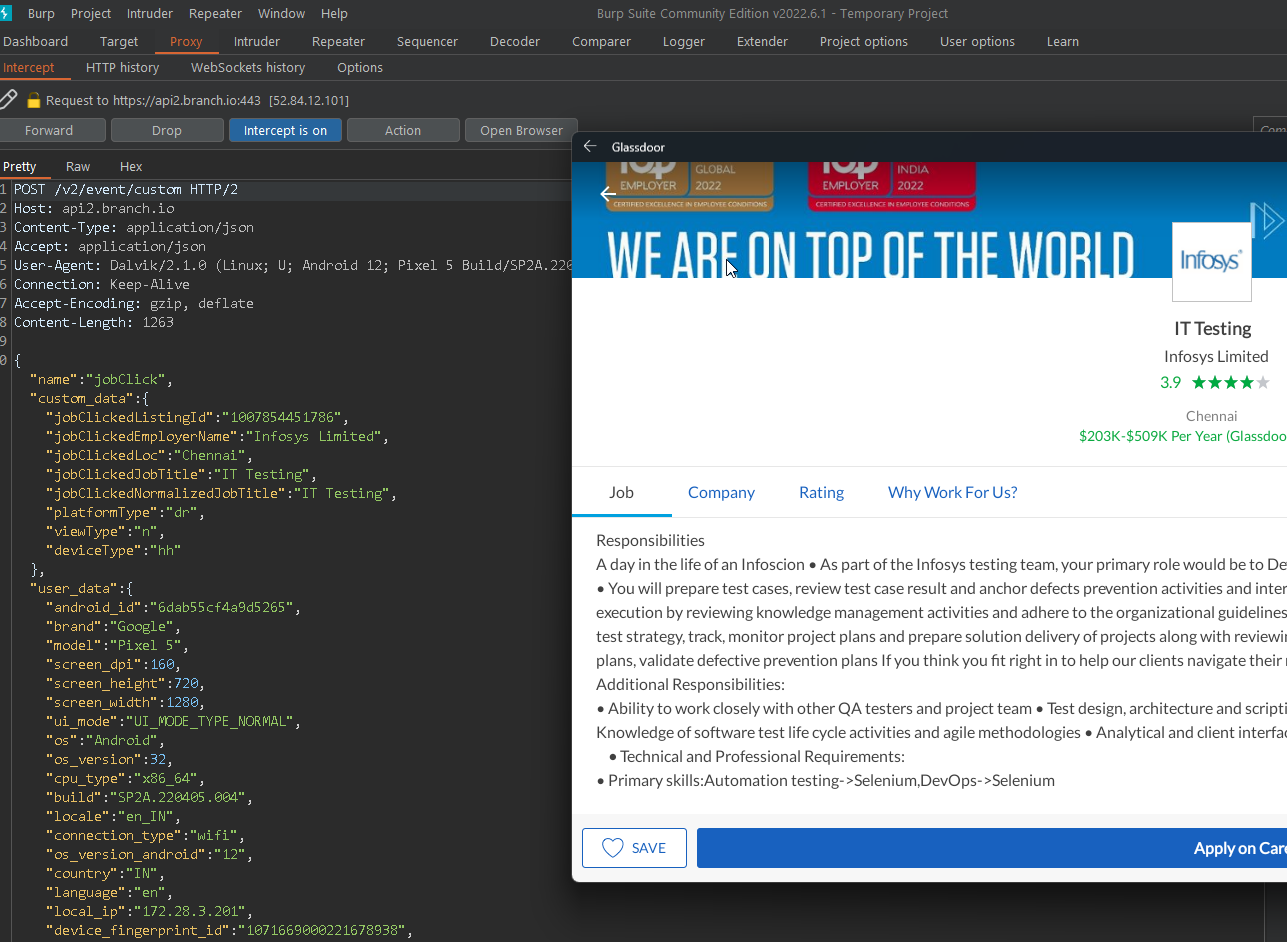
You should see some requests coming to burp now but many apps have ssl cert pinned and we cannot use our cert to decrypt the traffic. So we need a bypass for that, this is where ssl pinning bypass comes in.
objection --gadget com.glassdoor.app explore -s 'android sslpinning disable'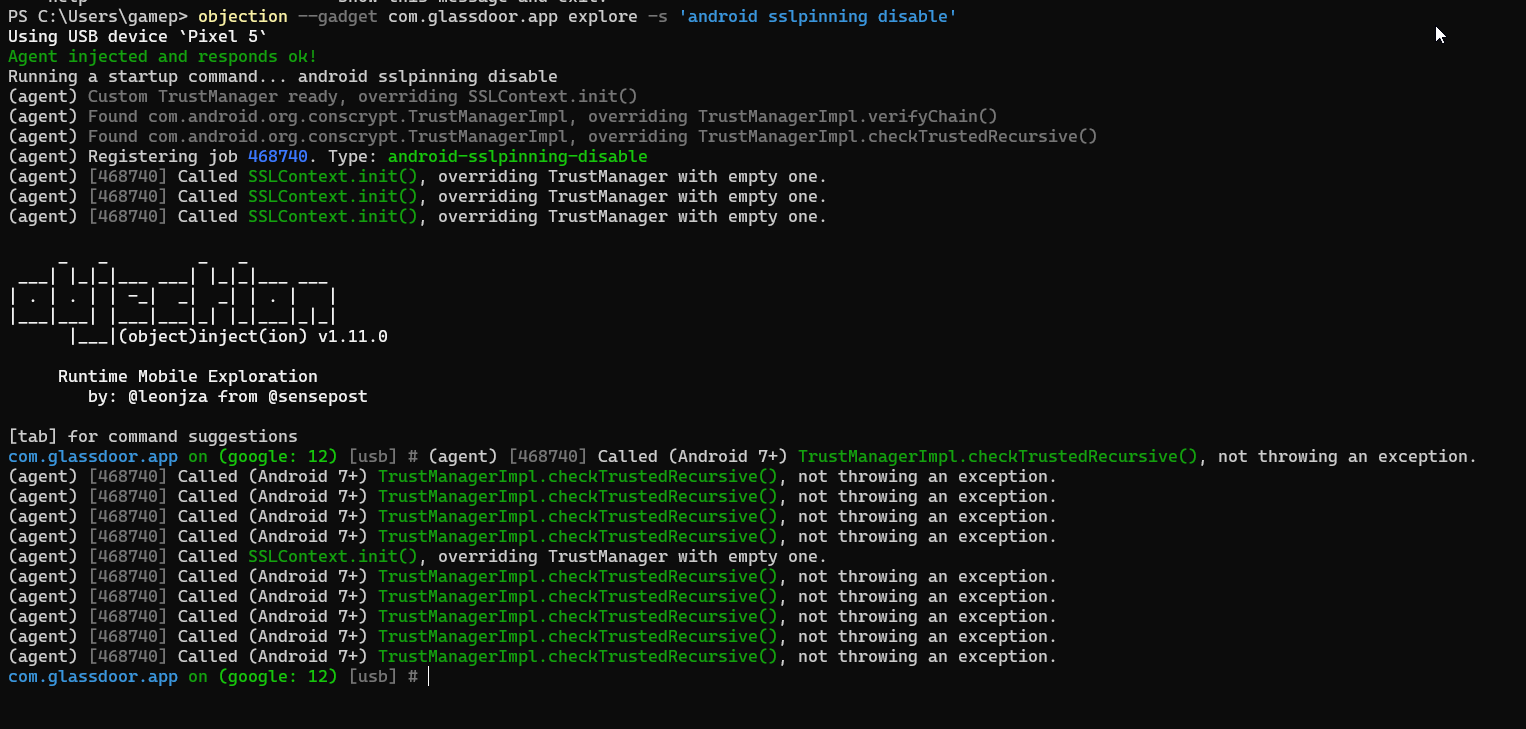
The app should automatically launch and now we can inspect the traffic.